Distributed Energy Generation Gateway (In)Security
Distributed energy generation (DEG) is a term used to describe the shift from centralized energy generation, such as power companies, to a source — typically a renewable energy source — closer to the user. It is most often seen in the form of solar panels on the rooftops of houses or office buildings, but DEG also includes wind turbines installed on farms, micro-hydro generators on properties with streams or rivers running through them, and natural gas turbines. DEG has gained significant traction over the past two decades because it allows residents and businesses to generate their own electricity and offset some of their expenses. Due to the increased use of DEG, we decided to investigate DEG device security focusing on solar devices because of their popularity.
Inverters and their communication modules are critical parts of the distributed energy industry. These devices, which form the backbone of household energy generation systems, have complex infrastructures that can make them vulnerable to potential security risks. This report provides an in-depth look at several leading DEG brands in the industry, examines their security practices, and identifies potential vulnerabilities.
Our investigation found that many vendors have adopted either HTTPS or proprietary encryption over HTTP, and performed a thorough inspection of the root certificate, which is a crucial step in ensuring secure communication. We would like to give a special mention to Victron Energy for their use of open-source software and their transparency in publishing their source code, which allowed us to conduct a very detailed inspection and allowed us to perform a comprehensive assessment of potential security issues. In addition to device vulnerabilities, we delve into encryption practices and data ownership concerns.
Device overview
We spent a few days analyzing devices from five different vendors. We chose to look at Enphase, Outback, and Sol-Ark due to their popularity in the United States. Phocos and Victron were added to our list of devices because we had access to them via the All Energies lab. Specifically, the devices we evaluated were the network gateways of solar or photovoltaic (PV) systems. Depending on the vendor, the gateways can be standalone, integrated with the microinverter, or integrated with the display panel. We focused on the following:
- The communication protocols
- The hardware
- The software and communication vulnerabilities
- The user interface (UI)
Table 1 provides a quick overview of these devices and information on their respective cloud services.
| Vendor | Enphase | Outback | Phocos | Sol-Ark | Victron |
| Model | Envoy IQ Combiner | MATE3s | Any-Bridge | PowerView WiFi Plus Ethernet Dongle | Cerbo GX |
| Encryption | Proprietary over HTTP | Proprietary over HTTP | TLS 1.2 + Root CA | No encryption | TLS 1.3 + Root CA |
| Cloud service provider | AWS | Azure | ammp.io | Alibaba Cloud | AWS |
| Cloud service control | Yes | Yes | No | Unknown | Yes |
| Web/command line interface (CLI) access | HTTP | HTTP, Telnet | Mobile app | PowerView (web) | NoVNC over HTTPS |
| Number of devices exposed on Shodan | 841 | 109 | 0 | 0 | 318 |
Table 1. DEG device overview (Data as of July 2023)
Security issues
Based on our analysis, these devices have various issues that can be grouped into six main categories. These devices and the respective categories in which they belong are listed in Table 2. Below Table 2 is a summary of the different issues, the devices that are affected by them, and detailed information on each device.
| Enphase Envoy IQ Combiner | Outback MATE3s | Phocos Any-Bridge | Sol-Ark PowerView WiFi Plus Ethernet Dongle | Victron Cerbo GX | |
| Password issues | X | X | |||
| Trusted local area network (LAN) | X | ||||
| Remote shutdown / Configuration | X | X | X | ||
| AP scans | X | X | |||
| Insecure firmware update | X | ||||
| Insecure communication | X | ||||
| Data sovereignty | AWS | Azure in Brazil | Netherlands | Aliyun in China | AWS |
Table 2. An overview of DEG devices and common issues
Password issues
Default and blank passwords are old and pervasive security issues with networked devices. Most devices either have a password printed on the device or require the user to change the password upon initial setup. If the user is not forced to set or change the default password, it will often remain as is or blank. Some companies generate the default password based on a hardware identifier, such as a serial number or MAC address. If that identifier is public information and the algorithm to generate the default password is discovered or reverse engineered, the password’s effectiveness is severely reduced.
Enphase
Enphase uses a computed default password based on the serial number of its communication gateway. The password is computed from the hashed serial number and a fixed seed. A custom algorithm is then implemented to get a default password of eight characters. The Enphase Installer Toolkit mobile app has already been reverse engineered to determine the exact algorithm for computing the default password.
To retrieve the serial numbers of Enphase Gateway, a user only needs to visit the Enphase web portal and, depending on the version of the Enphase Gateway, get the serial number from the HTML title or body. Figure 1 shows the serial number of Enphase Envoy gateway on its HTML title.
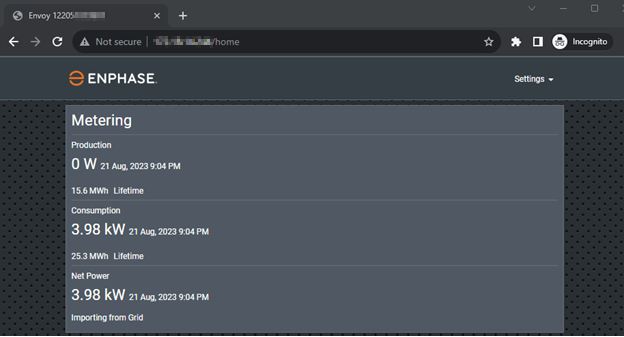
Figure 1. The serial number used to calculate the default password is found in the HTML Title
When a user is authenticated using the username “installer” and the computed default password, they can assume the role of an installer and can enable or disable power production and associate or disassociate microinverters or batteries in the PV system. These are just some of the capabilities of a user with installer capabilities, which can impact energy generation on these devices. This will be discussed in succeeding sections.
After our testing, Enphase released a firmware update that changed the method used for the device’s initial authentication. While this update appears to address the issue of the computed default password, there are still many exposed Envoy devices running the outdated firmware version.
Victron
Victron users can optionally set an authentication password to protect the front panel as well as remote access from unauthorized access. However, many users accepted the default setting (which is the no-password option), leaving the device vulnerable to unauthorized panel access and possibly unauthorized remote access. This could be the result of the installer or homeowner not setting the password.
Certain users opt not to authenticate access under the assumption that the physical access to the front panel is blocked. However, if devices are unintentionally exposed online, an attacker could easily connect to the device and use the built-in NoVNC service as if they were physically present at the control panel. The panel and the NoVNC service share the same password and depend on Victron’s App Server for authentication and the appropriate remote session selection.
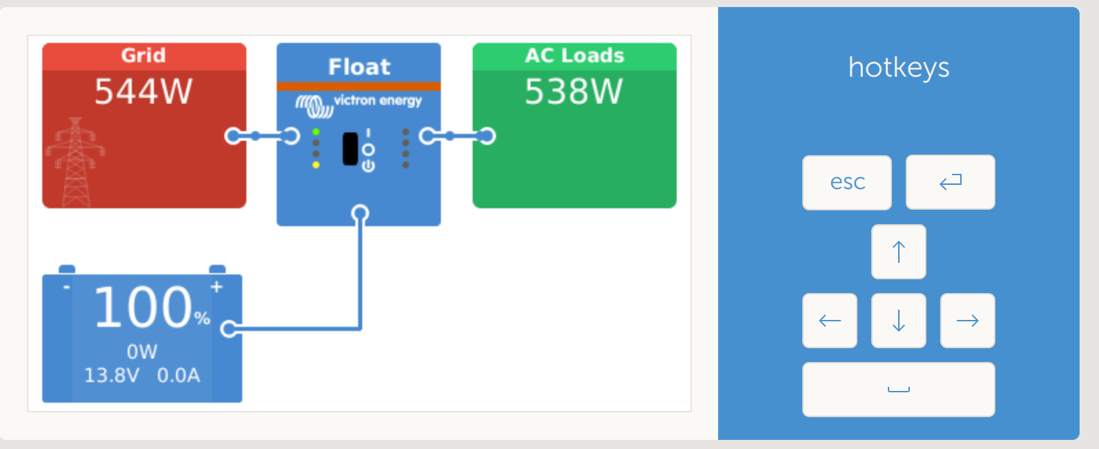
Figure 2. Internet-exposed unauthenticated Victron device found in Shodan
Exposing the device to the internet is not recommended, as Victron App Server provides a more secure way to access the device remotely. However, a password should be set regardless if the device is internet-exposed or otherwise.
Trusted LAN
Occasionally, vendors create devices that trust all LAN traffic, which might look reasonable in certain situations. However, bad actors can use a reflexive attack or launch malware to target LAN devices. Alternatively, if the devices are exposed to the internet, either on purpose or because of poor network configuration, anyone can change the settings on the UI.
Sol-Ark
Sol-Ark assumes all traffic from LAN is benign. Therefore, it should not be exposed to the internet, otherwise an attacker can collect information from the device, such as the inverter’s serial number, the Wi-Fi dongle’s key, and other fields.
Curl -XPOST 'http://[SOL-ARK_IP]/config?command=devinfo' --referer 'index.html'
{
"sn": "E4A0122xxxxx",
"key": "XPWRxxxx",
"hw": "AEM2-0000-06",
"sw": "487012xxxxx",
"g4status": 0,
"apn": "", "username": "",
"password": "",
"ethmoudle": 0,
"g4moudle": -1
}
Remote shutdown and configuration
Some of the devices we tested can be either shut down or reconfigured remotely. Unfortunately, when devices can be reconfigured remotely, there is a potential for inconvenience or damage: For example, the power generation could be discontinued, which would then cause a device to use grid power and, subsequently, waste money. In addition, when devices are remotely reconfigured, their inverters could be disassociated, their batteries could become drained, and their operating frequencies could be changed. Based on these potential effects, the main impact is likely financial in nature if the system is grid-connected. However, if the system is off-grid, remote reconfiguration could result in power losses and have other effects depending on what is connected to the system.
Enphase
Using the previously discussed computed password, a user with malicious intent can simply turn off the energy production feature of any exposed Enphase Envoy device that still uses the default password. The curl command below turns off the PV system’s power production capability.
curl --digest -u installer:[DEFAULT_PASSWORD] -X PUT \
http://[ENPHASE_IP]/ivp/mod/603980032/mode/power \
-d '{"length":1,"arr":[1]}'
Sol-Ark
An attacker can keep rebooting a Sol-Ark inverter by using the following command:
curl -XPOST 'http://[SOL-ARK_IP]sol-ark-IP/config?command=reboot' --referer 'index.html'
As there is no authentication, the inverter can be continuously rebooted, effectively causing a denial-of-service attack.
Victron
If a Victron device is not password-protected, everyone who has access to its homepage could simply use the on-screen navigation to change the configuration or shut down the device. Victron users may also use a credential-protected mobile application to access the same panel. Figure 3 shows that users can remotely upgrade the firmware or shut down an exposed and unauthenticated Victron device.
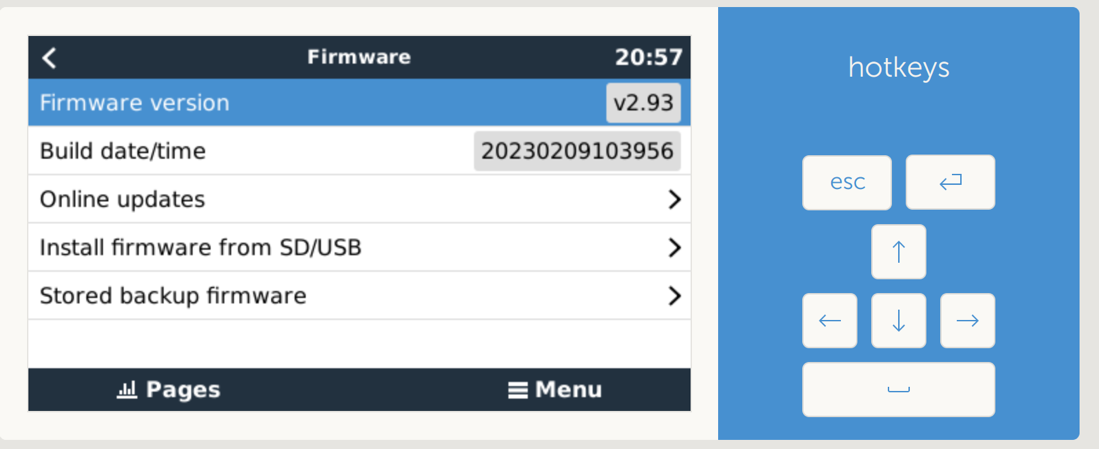
Figure 3. An unprotected Victron interface found on Shodan
Access point (AP) scans
An AP scanner is commonly used on Wi-Fi-connected network devices, which allows devices to easily connect to a wireless network. An unprotected device that has this feature can potentially give away its physical location. If an adversary were to gain access to the AP scan list, they could use that list to search public Wi-Fi AP scans like WiGLE (Wireless Geographic Logging Engine). The WiGLE service maps APs to latitude and longitude coordinates, which can allow malicious actors to find the physical location of a device, giving them detailed information that they can use to attack a specific neighborhood or region.
Enphase
By using the computed default password, a simple curl command will list APs that are in the vicinity of the gateway device.
curl --digest -u installer:[DEFAULT_PASSWORD] http://[ENPHASE_IP]/admin/lib/wireless_display.json
{
"supported": true,
"present": true,
"configured": true,
"up": true,
"carrier": true,
"current_network": {
"ssid": "Home Network",
"status": "connected",
"ip_address": "192.168.10.244",
"gateway_ip": "192.168.10.1",...
},
... "sites": [
{
"is_current_ssid": false, "ssid": "Other Network",
...
},
{
"is_current_ssid": true, "ssid": "Home Network",...
}
]
}
Sol-Ark
The Sol-Ark web interface also provides an AP scanning feature that an unauthenticated user can abuse to obtain a list of nearby APs using this curl command:
# curl 'http://[SOL-ARK_IP]/wifiscan.cgi' --referer 'index.html'
{
"num": 1,
"ap": [{
"ssid": "sweet home AP",
"rssi": -29
}]
}
Insecure firmware updates
Being able to update a device’s firmware can keep devices running securely as well as enable it to add new and updated features. On some devices, the user can request the device to update its firmware by downloading it directly from the server, while on others, the user would need to go to the manufacturer’s website to download the firmware then manually upload it to the device.
In the case of Sol-Ark, the company requires that a request be made to their customer service team to initiate the firmware update process from their end. As the firmware is the core software component for these devices, it’s important that the firmware update process remain secure.
Sol-Ark
Instead of the usual automated updates or users downloading updates from company websites, Sol-Ark provides a "remote firmware update" to its users.
In our investigation, we requested Sol-Ark's customer service to perform a remote firmware upgrade. To initiate our request, a customer service representative asked for proof that we were legitimate customers, which was a wise precaution. However, they asked for the solar plant and serial numbers and the key that’s printed on the Wi-Fi dongle. The last two items are also transmitted over the internet in plain text, making this authentication process trivial.
Moreover, the customer service representative triggered a remote update via a clear-text command, making the Wi-Fi dongle download the firmware from a URL over unencrypted HTTP. Based on our analysis, the firmware is downloaded from a Hong Kong-hosted server.
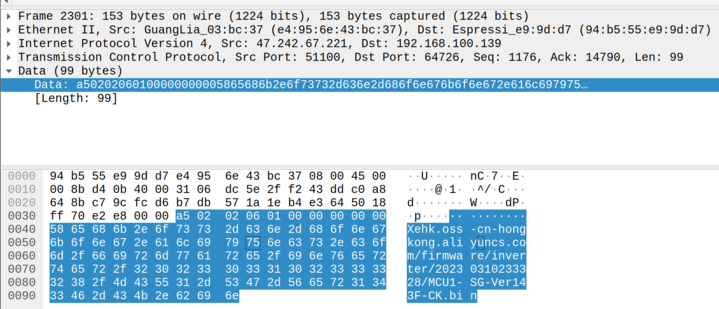
Figure 4. A packet capture showing the firmware download initiation process
We learned that this is not the firmware of the Wi-Fi dongle (an ESP32). The upgraded firmware is the communication firmware that runs inside the string inverter. If an attacker injects the firmware update command (unencrypted, unauthenticated), the Wi-Fi dongle can download it from the spoofed URL and update, potentially bricking the inverter or inserting malicious firmware.
Insecure communication
Communicating with cloud services typically involve accessing critical device information, system status information, and a list of commands. If the communication is not properly secured, an adversary could change the data and negatively impact the system.
Sol-Ark
Sol-Ark sends data to one of the four Aliyun servers, the Alibaba cloud computing service that’s hosted in China. This is possibly because both the Sol-Ark Wi-Fi dongle and its energy management system are supplied by an original equipment manufacturer (OEM) called E-Linter, a Chinese company.

Figure 5. A packet capture showing important device information
From the packet dumps, we can see data being transmitted in plain text at port 51100. The data reads:
| Data | Description |
| E4A0XXXXXXXX | The device serial number |
| XPWRXXXX | The Wi-Fi dongle's key; this information is needed to initiate a remote firmware update |
| EESE-D200 | The Wi-Fi dongle's model name |
| 12345678 | The Wi-Fi password |
| 2209XXXXXX | The serial number of the string inverter to which the device is connected |
| STROG INV | The model name of the string inverter to which the device is connected |
| 7.2.2.2 | The firmware version of Sol-Ark 15kW |
| 1.4.3.E | Comm version; this module was updated in "scheduled remote firmware upgrade" |
Data sovereignty
Governments, companies, and users of these devices may be concerned about where their data is going, where it’s being stored, and who has access to it. Some governments even have regulations regarding data sovereignty. Based on our observation, Enphase and Victron sends data to Amazon Web Services (AWS) based in the US or EU. The servers for Outback are located on Microsoft’s Azure platform in Brazil. Meanwhile, Phocos transmits data to the Netherlands and Sol-Ark to China.
Sol-Ark
Sol-Ark sends data to “iot.e-linter.com.” At the time of writing, the domain resolves to the following IP addresses, which are located on Aliyun (Alibaba Cloud) in China:
- 47.242.67.221
- 47.244.29.210
- 121.40.236.68
- 47.97.195.241
While we acknowledge that it’s normal practice for companies to send data to vendors or other third-parties, this can cause issues for those who have concerns or restrictions on data sovereignty.
Sol-Ark's energy management system is outsourced to E-Linter, who owns the following domains:
- e-linter.com (the OEM of the PowerView mobile app and Sol-Ark’s IoT products)
- cloud.ledvance-re.com (LEDVANCE or mySYLVANIA, a company that sells LED and traditional lighting products to the US and Canada)
- sunsynk.net (a company that mainly sells solar inverters in South Africa)
- ftp.gleanergy-solutions.com (a company based in in North York, ON, Canada)
Additionally, Deye, which is one of the hardware manufacturers of Sol-Ark, also supplies hardware to Sunsynk (South Africa).
Large-scale outages via the cloud
While it may seem appealing for attackers to target individual exposed devices, it is not an efficient method for causing large-scale outages on distributed energy generation devices. Even though attackers may still be able to access the devices using other attack methods via the LAN, the implementation of network segments and firewalling can help minimize attacks from the LAN.
Instead, attackers may opt to target cloud services that manage and control multiple devices at once, resulting in potentially controlling them for nefarious purposes. It is important to note that cloud service providers have their own security measures in place to help prevent such attacks from happening.
Attackers can target accounts with remote management capabilities, such as PV systems’ installers, using a variety of methods, including phishing, password brute-forcing, and exploiting known vulnerabilities. Once the attackers have gained access, they can manipulate the data and remotely control the installations where those cloud services allow control.
The Dutch Institute for Vulnerability Disclosure (DIVD) case DIVD-2022-00009 details how security researchers found and used Solarman cloud administrator credentials that can allow them to deploy remote firmware updates to almost one million installations, generating over 10 gigawatts (GW) of power.
Conclusion
During our investigation, many of the devices we looked at did a respectable job of protecting the device and the communication path between the device and the cloud service. Our evaluation did not find any issues on the Outback MATE3s and the Phocos Any-Bridge. The Victron Cerbo GX, if configured with a password, had particularly good security. If the Enphase Envoy’s default computed password is changed, it significantly reduces the number of security issues. The Sol-Ark device had the most security concerns.
It should be noted that we did not assess the security of the cloud services. We would like to remind the reader that if the cloud service allows for control, this may be an area to pay attention to when selecting or securing your device.
As we’ve previously mentioned, if the user is concerned about risks surrounding the country or cloud service provider these services use, this might be something they should consider when evaluating the security of these DEG platforms. As DEG continues to grow, the question of individual device security becomes a little less important while overall vendor security becomes more prominent. If an adversary can disable the generation for an entire vendor or multiple vendors in a region, how will that impact the grid in that region or across multiple neighboring regions? Power companies currently have methods to deal with sudden increased demands and outages, but are those methods scalable and can they keep up as distributed energy generation increases? Will the energy companies implement technologies to remotely control grid-connected DEG systems?
Suggestions and best practices
- Limit remote access. Do not expose the controller interface to the internet. Verify whether the vendor can control devices through cloud services, and if so whether it is secure communication.
- Change the default password and setup password protection features.
- Segregate the inverter’s network interface from the LAN, especially if the device trusts LAN.
- Users who are not as technically proficient can check out best practices and may be able to receive assistance from the installer. However, users should exercise caution as some installers may not be security conscious.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 MQTT and M2M: Do You Know Who Owns Your Machine’s Data?
MQTT and M2M: Do You Know Who Owns Your Machine’s Data? Building Resilience: 2024 Security Predictions for the Cloud
Building Resilience: 2024 Security Predictions for the Cloud Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023
Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023 Mitigating the Threat of Sidecar Container Injection
Mitigating the Threat of Sidecar Container Injection