CHALLENGES
Operationalizing zero trust
Zero trust is complex. It requires a comprehensive understanding of networked assets, user behavior, and data flows. Without visibility into these areas, identifying and addressing potential security risks can leave businesses vulnerable to exploits. Legacy systems, applications, and devices make it difficult to assess risk across the enterprise.
How organizations are developing their Zero Trust strategies:
ESG surveyed 379 IT and cybersecurity professionals in North America involved with technology and processes supporting zero trust. Key data points:
- $675k reduction in average security costs.
- Reduces the number of data breaches by 34% and cyber incidents by 32%
- Lowered their mean time to respond (MTTR) by 10 days!

Accurately assessing risk exposure
It's crucial to have a thorough understanding of the potential risks and exposure your enterprise faces. Knowing these risks can help you make informed decisions and take proactive measures to mitigate them. Uncertainty or ignorance can leave your business vulnerable.
Implementing zero-trust strategies
Consolidating visibility and conducting real-time risk assessments while incorporating people, processes, and technology are daunting tasks. Without the right in-house resources and skillsets, they can be even tougher.

Finding the right fit
Implementing a zero-trust model while incorporating existing technologies can be a challenge without a platform approach consolidating visibility and analytics across your enterprise.
SOLUTIONS
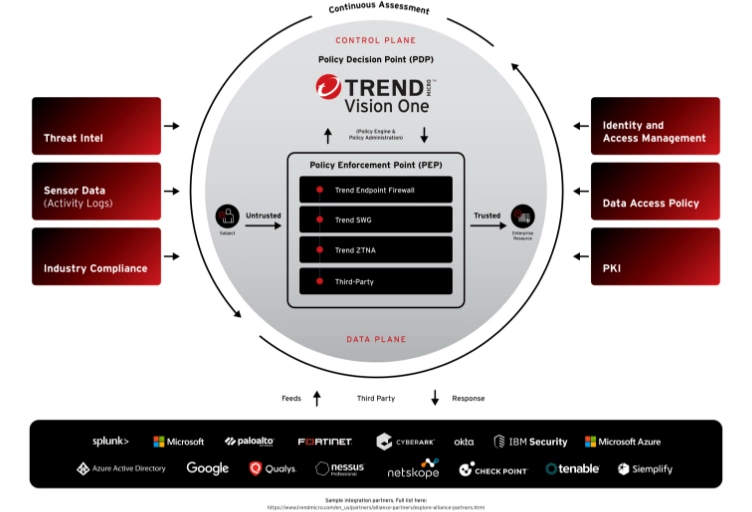
Simplify zero-trust security with Trend Vision One™
Start with a solid foundation of zero-trust architecture aligned with industry best practices. Understand your attack surface, assess your risk in real time, and adjust policies across network, workloads, and devices from a single console. Integrate best-in-class technologies from our ecosystem partners to seamlessly operationalize zero trust.
Pinpoint every entity
Ensure complete transparency and maintain an accurate, real-time inventory of all resources. Detect individuals’ and devices’ publicly accessible domains, IP addresses, cloud-based applications, cloud storage, containers, and tasks across both external and internal company networks.
Accurately assess every risk
Understand your overall enterprise risk and dive deep into specific risk factors and considerations, including asset criticality, vulnerabilities, security posture, threat activity, and exposure. Leverage automated risk scoring, trending, and industry benchmarks to identify priority security initiatives and actions.
Centralize every action
Streamline security and reduce zero-trust complexity. Easily monitor, manage, adjust, and execute data-driven security controls. Ease the burden on teams while focusing on higher-level tasks with automation and orchestration, all in a single console.
Enrich existing security solutions
Augment current processes and integrate new or existing best-in-class technologies with our growing list of partners. Our ecosystem-friendly platform approach consolidates key zero-trust implementations like SWG, CASB, and ZTNA with XDR and attack surface management solutions with third-party integrations and APIs to deliver flexibility and ease adoption.
Zero-Trust Architecture
Build a stronger, more resilient security posture
Protect, prevent, detect, and close security gaps fast with zero trust. Explore your unique zero-trust use cases with Trend experts.

Protect hybrid workforces
Automatically block connections based on machine learning, custom policies, and dynamic risk assessment. Maintain configuration best practices, enforce policies and security controls, and prevent lateral movement of unauthorized activity. Zero trust reduces the risk of data breaches by limiting exposure of sensitive data to only those who absolutely need it.

Provide secure access
Develop a flexible zero-trust security framework tailored to your organization. Create static (least privilege) and dynamic (conditional) rules for user groups and specific access, application-specific controls, time-based policies, geolocation-based access, individual device posture restrictions, and risk score-based policies.

Achieve extended visibility
Use activity data from networks, workloads, SaaS apps, and workstations to assess risks. Proactively block known malware, network exploitable vulnerabilities – including Zero Day and exfiltration techniques – through continuous monitoring, anomaly detection, and pre-emptive threat protection.

Optimize cyber insurance
Earn better cyber insurance premiums by demonstrating that your organization is proactively managing risk and preventing cyberattacks with zero trust. Provide evidence of multi-factor authentication (MFA), network micro-segmentation, and continuous risk assessment and monitoring.

Reduce complexity
Realize significant business and operational benefits and support a zero-trust strategy by consolidating cybersecurity tools. By reducing the complexity of managing multiple solutions, organizations can minimize costs while easing operational and compliance complexity through unified policy management.
Have a unique use case?
Get in touch with our experts
“Organizations starting their ZT [Zero Trust] journey and needing a solution for advanced visibility and analytics to establish a baseline should evaluate Trend Micro.”

INDUSTRY STATISTICS
The impact of blind spots
Enterprises face significant challenges with the constantly evolving digital attack surface. By aligning with zero-trust best practices and implementing controls engineered into a single platform, organizations can build a stronger and more resilient security posture. This approach can effectively close security gaps, while proactively meeting regulatory and compliance requirements, leading to a more secure and robust digital environment.
39%
of organizations struggle with the changing digital attack surface
Trend Micro
10%
of enterprises should maintain zero-trust programs by 2026
Gartner
51%
of organizations have adopted zero-trust security strategies
Ponemon
62%
of respondents reported “significant” security improvement with a zero-trust strategy
Trend Micro
JOIN 500 MILLION USERS
Your zero-trust journey is complex.
Entrust it to the experts.

